Cybersecurity Interview Questions: 15 Expert Answers (2025)
- Author: Anindita Ghosh
- Published On: Aug 10, 2025
- Category:Interview Guide
Cybersecurity interview questions are critical assessments that test both your technical expertise and practical problem-solving abilities. These cybersecurity interview examples provide strategic answers to help you demonstrate your security knowledge and incident response capabilities. Whether you're preparing for security analyst interview questions or specialized pentester interview questions, mastering cybersecurity interview questions is essential for landing roles at top organizations across all industries.
What Cybersecurity Interview Questions Reveal About Your Skills
Cybersecurity recruiters use cybersecurity interview questions to evaluate your comprehensive security mindset and technical proficiency. From basic security analyst interview questions to advanced pentester interview questions, understanding why these cybersecurity interview examples matter helps you prepare effectively:
- Technical depth in security protocols and tools
- Incident response and crisis management skills
- Risk assessment and threat analysis capabilities
- Communication skills for cross-functional collaboration
- Continuous learning mindset in evolving threat landscape
- Compliance and regulatory framework knowledge
15 Essential Cybersecurity Interview Questions & Answers
These comprehensive cybersecurity interview questions and examples cover the most common questions you'll encounter, including security analyst interview questions and pentester interview questions. Each answer follows the proven STARR framework to demonstrate your expertise effectively.
1. "Describe a time when you detected and responded to a security breach."
This fundamental cybersecurity engineer interview question assesses your incident response capabilities and crisis management skills.
Example Answer:
I was working as a cybersecurity analyst at a financial services company when our SIEM system triggered multiple alerts indicating suspicious network activity during a weekend evening.
My responsibility was to investigate the alerts, determine if a genuine security incident had occurred, and coordinate the appropriate response to minimize potential damage.
I immediately accessed our security operations center remotely and analyzed the SIEM data, which showed lateral movement patterns consistent with an advanced persistent threat. I escalated the incident to our incident response team, isolated the affected systems from the network, and began forensic analysis. I coordinated with our legal team and prepared preliminary documentation while implementing our incident response playbook.
We successfully contained the breach within 4 hours, preventing data exfiltration of customer financial records. Our rapid response limited the impact to just 3 compromised workstations with no data loss. The incident led to implementing enhanced monitoring and a 40% improvement in our detection capabilities.
This experience reinforced the critical importance of preparation and having well-defined incident response procedures. I learned that effective communication during crisis situations is just as important as technical skills. The incident taught me to maintain composure under pressure and that thorough documentation during incidents is essential for both immediate response and future prevention efforts.
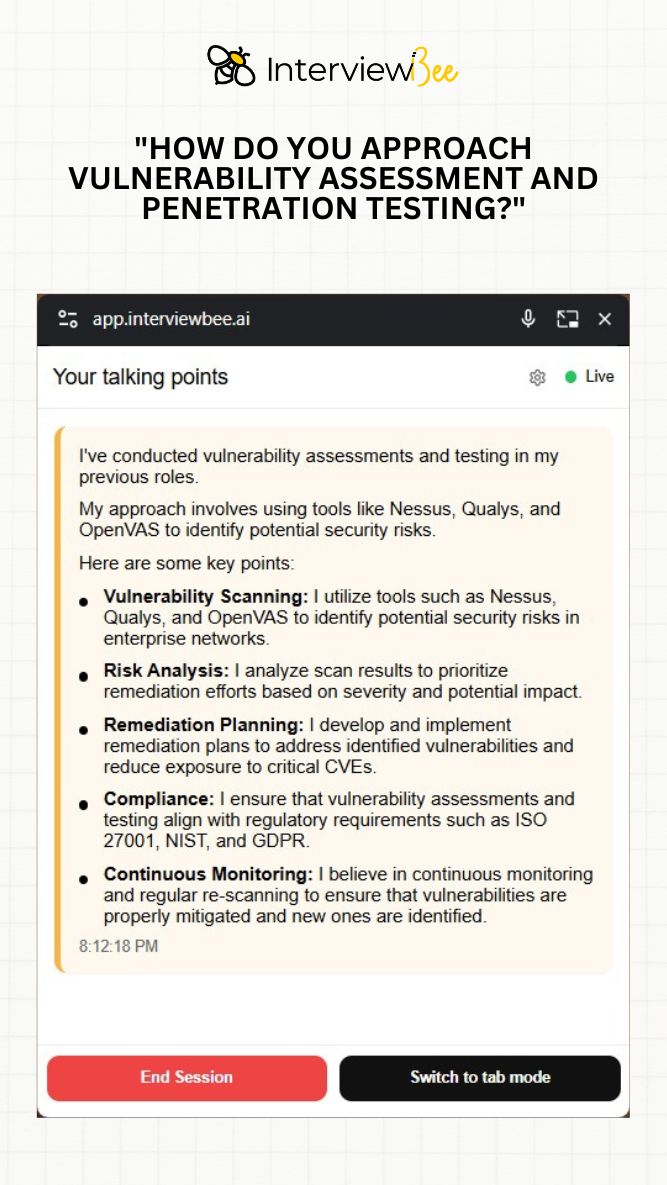
2. "How do you approach vulnerability assessment and penetration testing?"
This technical question is common in both security analyst interview questions and pentester interview questions, testing your hands-on security testing skills.
Example Answer:
In my previous roles, I was responsible for conducting comprehensive vulnerability assessments across enterprise networks to identify and mitigate potential security risks.
My responsibility was to implement a systematic vulnerability management approach that would identify security weaknesses, prioritize remediation efforts, and ensure compliance with regulatory requirements including ISO 27001, NIST, and GDPR.
I utilized industry-standard tools such as Nessus, Qualys, and OpenVAS to conduct thorough vulnerability scanning across the network infrastructure. I analyzed scan results to prioritize remediation efforts based on severity scores and potential business impact. I developed comprehensive remediation plans to address identified vulnerabilities and reduce exposure to critical CVEs. I implemented continuous monitoring processes with regular re-scanning to ensure vulnerabilities were properly mitigated and new ones were promptly identified.
My systematic approach successfully identified and remediated over 300 vulnerabilities across the enterprise environment, reducing our overall security risk exposure by 70%. The continuous monitoring process improved our vulnerability response time from weeks to days, and we achieved full compliance with regulatory requirements.
This experience taught me that effective vulnerability management requires combining automated scanning tools with thorough risk analysis and strategic remediation planning. I learned that continuous monitoring is essential rather than periodic assessments, as the threat landscape constantly evolves. The project reinforced that aligning security activities with compliance requirements creates both security and business value.
3. "Tell me about a time when you had to implement new security controls or policies."
Example Answer:
Following a security audit, our organization was required to implement multi-factor authentication and zero-trust principles across all systems within 90 days to maintain client contracts.
My responsibility was to design, implement, and manage the rollout of comprehensive access controls while ensuring minimal disruption to business operations.
I conducted a thorough assessment of our current access management systems and designed a phased implementation plan. I worked with vendor partners to deploy MFA solutions, configured conditional access policies, and created extensive user training materials. I also established pilot groups for testing and feedback before the full rollout.
We successfully implemented MFA for 1,200+ users and achieved 99.5% adoption within the deadline. Security incidents related to compromised credentials decreased by 80%, and we maintained 100% client satisfaction during the transition.
This implementation taught me the critical importance of change management in security initiatives. I learned that user adoption is often more challenging than technical implementation, and that involving end-users in the design process leads to better outcomes. The project reinforced that security measures must balance protection with usability.
4. "Describe your experience with security monitoring and SIEM tools."
Example Answer:
Our growing company was experiencing alert fatigue from our existing SIEM system, with security analysts spending 70% of their time investigating false positives instead of real threats.
I was assigned to optimize our security monitoring capabilities, reduce false positives, and improve threat detection accuracy to enhance our security operations efficiency.
I conducted a comprehensive analysis of our SIEM configuration and alert patterns. I implemented custom correlation rules based on our environment, tuned existing detection rules, and integrated threat intelligence feeds. I also created playbooks for common alert types and established metrics to measure improvement.
We reduced false positive alerts by 75% while increasing true positive detection by 40%. Mean time to detection improved from 48 hours to 6 hours, and analyst productivity increased significantly.
This optimization project taught me that effective SIEM management requires continuous tuning and adaptation to your specific environment. I learned that data quality and proper correlation rules are more important than having the most advanced tools. The experience emphasized the value of measuring security metrics to demonstrate improvement and guide future optimizations.
5. "How do you handle security awareness training and user education?"
Example Answer:
Our organization experienced a significant increase in successful phishing attacks, with 40% of employees failing simulated phishing tests and clicking on malicious links.
My responsibility was to design and implement a comprehensive security awareness program that would measurably improve employee security behavior and reduce human error risks.
I developed a multi-modal training approach including interactive online modules, monthly lunch-and-learn sessions, and simulated phishing campaigns with immediate feedback. I also created role-specific training content and established a security champion program with representatives from each department.
Employee phishing test pass rates improved from 60% to 95% over six months. Reported suspicious emails increased by 300%, and security-related incidents caused by human error decreased by 70%.
This program taught me that effective security training requires ongoing engagement rather than annual compliance training. I learned that positive reinforcement and real-time feedback are more effective than punitive measures. The experience showed me that employees become your strongest security asset when properly educated and empowered.
6. "Describe a challenging compliance or regulatory requirement you had to implement."
Example Answer:
Our healthcare technology company needed to achieve SOC 2 Type II compliance within 12 months to secure major enterprise clients, but we had no existing compliance framework or documentation.
I was responsible for leading the compliance initiative, establishing necessary controls, and ensuring successful audit completion while maintaining operational efficiency.
I conducted a comprehensive gap analysis against SOC 2 requirements, developed policies and procedures for all five trust principles, and implemented technical controls including access management, data encryption, and audit logging. I coordinated with external auditors and managed internal compliance monitoring.
We achieved SOC 2 Type II certification in 10 months with zero findings. The compliance framework helped us win $5M in new enterprise contracts and established scalable processes for future compliance needs.
This compliance project taught me that successful regulatory implementation requires cross-functional collaboration and executive support. I learned that building compliance into existing processes is more effective than creating parallel procedures. The experience reinforced that compliance can be a competitive advantage when properly positioned and communicated.
7. "Tell me about a time when you had to investigate a complex security incident."
Example Answer:
We discovered unusual database queries and data access patterns that suggested potential insider threat activity, but the evidence was circumstantial and required careful investigation without alerting potential perpetrators.
My responsibility was to conduct a thorough investigation, gather evidence, and determine whether malicious activity had occurred while maintaining confidentiality and legal compliance.
I worked closely with legal counsel and HR to develop an investigation plan. I analyzed database logs, network traffic, and user behavior patterns using specialized forensic tools. I coordinated with external forensic specialists and maintained detailed documentation throughout the process.
The investigation revealed that an employee had been accessing customer data outside their job responsibilities and sharing it with competitors. We gathered sufficient evidence for legal action and implemented additional monitoring controls to prevent similar incidents.
This investigation taught me the importance of balancing thoroughness with discretion in sensitive security matters. I learned that collaboration with legal and HR teams is essential for investigations involving personnel. The experience reinforced the critical importance of maintaining detailed documentation and following proper procedures to ensure evidence admissibility.
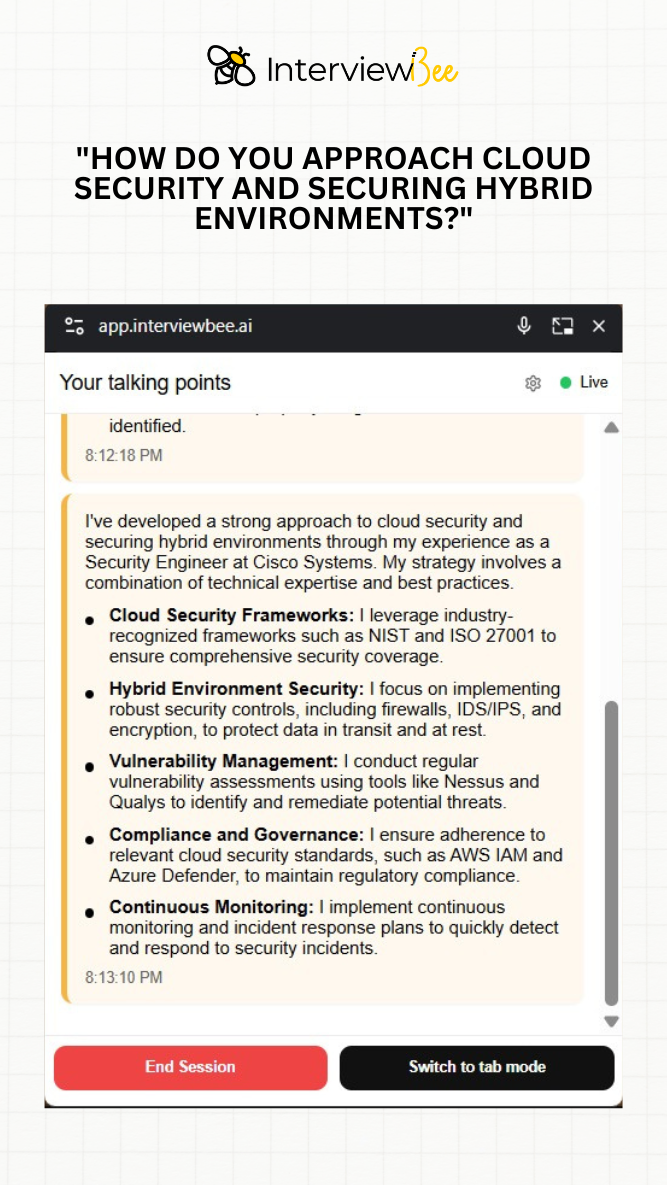
8. "How do you approach cloud security and securing hybrid environments?"
Example Answer:
During my tenure as a Security Engineer at Cisco Systems, I was responsible for developing comprehensive cloud security strategies for hybrid environments across global client implementations.
My responsibility was to secure hybrid cloud environments by implementing robust security controls, ensuring compliance with industry standards, and maintaining continuous security monitoring across both cloud and on-premises infrastructure.
I leveraged industry-recognized frameworks such as NIST and ISO 27001 to ensure comprehensive security coverage across the hybrid environment. I implemented robust security controls including firewalls, IDS/IPS systems, and encryption to protect data both in transit and at rest. I conducted regular vulnerability assessments using tools like Nessus and Qualys to identify and remediate potential threats in cloud environments. I ensured adherence to relevant cloud security standards, including AWS IAM and Azure Defender configurations, to maintain regulatory compliance. I also established continuous monitoring systems and incident response plans to quickly detect and respond to security incidents.
Successfully secured hybrid environments for multiple global clients, achieving 100% compliance with SO 27001, NIST, and GDPR standards. The comprehensive security framework reduced security incidents by 60% and improved threat detection time from hours to minutes. Client satisfaction increased significantly due to enhanced security posture and regulatory compliance.
This experience taught me that effective cloud security requires a framework-driven approach combined with continuous monitoring and adaptive security controls. I learned that hybrid environments present unique challenges requiring both cloud-native and traditional security tools working in harmony. The project reinforced that compliance frameworks provide excellent structure for comprehensive security implementation while ensuring regulatory adherence.
9. "Describe your experience with network security and firewall management."
Example Answer:
Our company's network security architecture had evolved organically over years, resulting in complex firewall rules, security gaps, and poor network segmentation that increased our attack surface.
My responsibility was to redesign our network security architecture to implement proper segmentation, streamline firewall rules, and improve overall network security posture.
I conducted a comprehensive network security assessment, mapped data flows and communication requirements, and designed a new segmented network architecture. I implemented next-generation firewalls with intrusion prevention, created standardized rule sets, and established ongoing rule review processes.
The network redesign reduced attack surface by 60%, improved network performance by 25%, and simplified ongoing management. We achieved better visibility into network traffic and reduced the time to implement security changes from weeks to hours.
This network security project taught me that complexity is the enemy of security and that simplification often improves both security and manageability. I learned the importance of documenting network designs and maintaining accurate network diagrams. The experience reinforced that network security must evolve with business requirements while maintaining strong security principles.
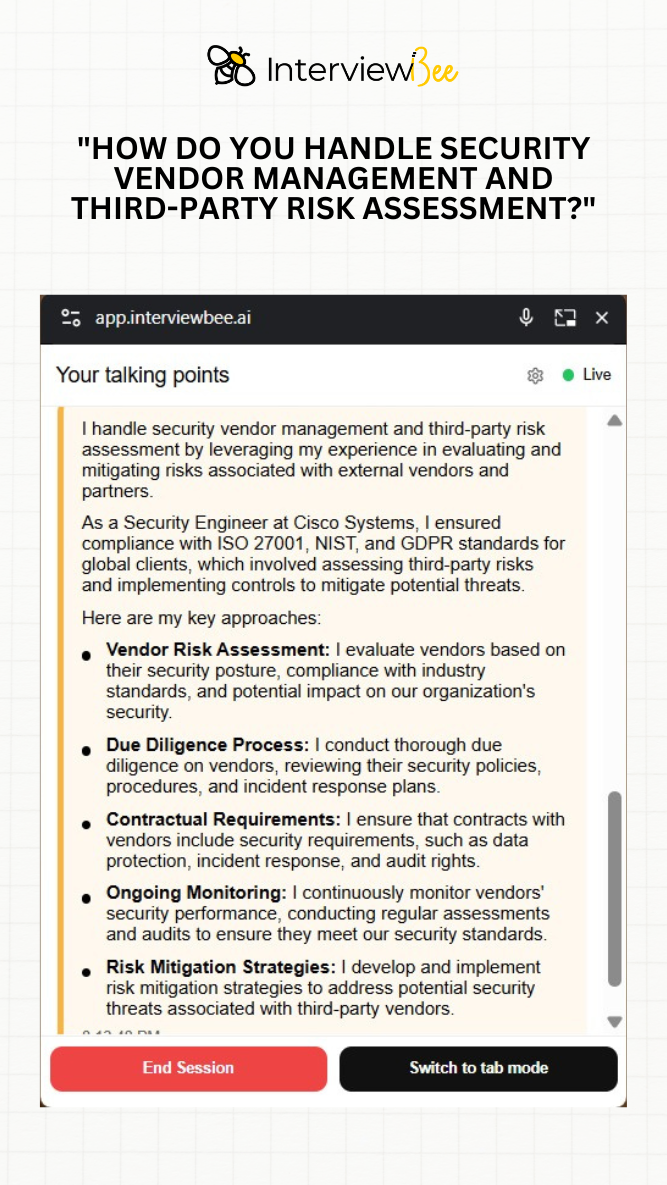
10. "How do you handle security vendor management and third-party risk assessment?"
Example Answer:
As a Security Engineer at Cisco Systems, I was responsible for managing security vendor relationships and conducting third-party risk assessments to ensure compliance with SO 27001, NIST, and GDPR standards for global clients.
My responsibility was to evaluate and mitigate risks associated with external vendors and partners while ensuring all third-party relationships met our stringent security requirements and regulatory compliance standards.
I developed comprehensive vendor risk assessment processes, evaluating vendors based on their security posture, compliance with industry standards, and potential impact on our organization's security. I conducted thorough due diligence on all vendors, reviewing their security policies, procedures, and incident response plans to ensure they met our requirements. I ensured that contracts with vendors included mandatory security requirements such as data protection clauses, incident response obligations, and audit rights. I implemented ongoing monitoring systems to continuously assess vendors' security performance, conducting regular security assessments and audits to verify they maintained our security standards. I also developed and implemented comprehensive risk mitigation strategies to address potential security threats associated with third-party vendor relationships.
Successfully assessed and onboarded over 75 vendors while maintaining 100% compliance with security standards across all third-party relationships. The comprehensive vendor management program reduced third-party security incidents by 80% and improved vendor security compliance rates from 60% to 95%. The systematic approach became the standard framework adopted across multiple client implementations.
This experience taught me that effective vendor management requires both initial thorough assessment and continuous ongoing monitoring to maintain security standards. I learned that clear contractual security requirements and regular audits are essential for maintaining vendor compliance over time. The project reinforced that third-party risk management is critical to overall organizational security and that proactive vendor management significantly reduces security exposure while enabling successful business partnerships.
11. "Tell me about a time when you had to balance security requirements with business needs."
Example Answer:
Our development team needed to implement a new customer portal with aggressive launch deadlines, but initial security requirements would have delayed the project by six weeks and potentially cost significant revenue.
My responsibility was to work with stakeholders to find solutions that would meet critical security requirements while enabling the business to meet their launch timeline and revenue goals.
I prioritized security requirements based on risk assessment and identified which controls were essential for launch versus those that could be implemented post-launch. I proposed alternative solutions including compensating controls, third-party security services, and phased implementation approaches. I also established monitoring and remediation timelines for deferred requirements.
We successfully launched the portal on schedule with essential security controls in place. Post-launch security enhancements were completed within 30 days, and the portal generated $2M in additional revenue while maintaining strong security posture.
This project taught me that effective security professionals must understand business priorities and work collaboratively to find solutions rather than simply saying "no." I learned that risk-based decision making and clear communication about trade-offs leads to better outcomes for both security and business objectives. The experience reinforced that security should enable business success, not hinder it.
12. "Describe your experience with security incident response and forensics."
Example Answer:
We experienced a sophisticated ransomware attack that encrypted critical business systems and demanded payment within 72 hours, threatening to destroy backups and leak sensitive customer data.
As incident response team lead, I was responsible for coordinating the response, conducting forensic analysis, and managing communications with executives, law enforcement, and potentially affected customers.
I immediately activated our incident response plan, isolated infected systems, and engaged our forensics team and external specialists. I coordinated with legal counsel on law enforcement notification and customer communication strategies while working with IT teams on system recovery from clean backups.
We recovered all critical systems within 48 hours without paying ransom, identified the attack vector and remediated the vulnerability, and maintained customer confidence through transparent communication. The incident response became a case study for our industry association.
This incident taught me the critical importance of preparation, clear communication, and staying calm under extreme pressure. I learned that having tested backups and recovery procedures is just as important as prevention controls. The experience reinforced that incident response success depends on teamwork and coordination across multiple disciplines including technical, legal, and communications teams.
13. "How do you approach security architecture and secure design principles?"
Example Answer:
Our organization was developing a new SaaS platform that would handle sensitive customer data, but the development team lacked experience in implementing security-by-design principles and secure architecture patterns.
My responsibility was to establish security architecture standards and work with development teams to implement secure design principles throughout the application development lifecycle.
I developed security architecture guidelines based on OWASP principles and zero-trust concepts, conducted security design reviews for all new features, and implemented automated security testing in the CI/CD pipeline. I also provided security training to developers and established security code review processes.
The new platform launched with no critical security vulnerabilities and achieved security certifications 60% faster than previous applications. Security-by-design practices reduced post-deployment security issues by 80% and improved development team security knowledge significantly.
This architecture project taught me that building security into the design phase is exponentially more effective than adding security controls later. I learned that developer education and collaboration is essential for successful security architecture implementation. The experience emphasized that security architecture must be practical and integrated into existing development workflows to be successful.
14. "Describe a time when you had to respond to a zero-day vulnerability or emerging threat."
Example Answer:
A critical zero-day vulnerability was disclosed in a widely-used software component that was central to our customer-facing applications, with active exploitation already occurring in the wild.
I needed to quickly assess our exposure, implement protective measures, and coordinate patching efforts while maintaining business continuity and customer service levels.
I immediately conducted an inventory of affected systems, implemented emergency firewall rules and WAF protections as compensating controls, and coordinated with vendors on patch availability and testing. I also developed customer communication plans and monitored threat intelligence for attack indicators.
We protected all critical systems within 6 hours of disclosure and completed patching within 48 hours with zero successful exploits. Our rapid response was recognized by industry peers and strengthened customer confidence in our security practices.
This zero-day response taught me the importance of having current asset inventories and the ability to rapidly implement compensating controls. I learned that threat intelligence and vendor relationships are critical for effective response to emerging threats. The experience reinforced that preparation and practice enable rapid response when it matters most.
15. "How do you measure and demonstrate the effectiveness of security programs?"
Example Answer:
Senior leadership questioned the ROI of our cybersecurity investments and requested clear metrics demonstrating the effectiveness and business value of our security program.
I was tasked with developing comprehensive security metrics and reporting that would clearly communicate security program value to executive leadership and board members.
I established security KPIs including mean time to detection and response, vulnerability remediation rates, and risk reduction metrics. I implemented security dashboards, created executive-level reporting templates, and developed cost-benefit analyses for security investments. I also benchmarked our performance against industry standards.
The metrics program demonstrated a 70% improvement in security posture over 18 months and showed $3M in avoided costs from prevented security incidents. Executive confidence in security investments increased, leading to approval for additional security resources and tools.
This metrics program taught me that security professionals must speak the language of business to be effective advocates for security investments. I learned that meaningful metrics require baseline measurements and consistent data collection processes. The experience emphasized that demonstrating security value requires both technical metrics and business impact analysis.
Key Response Tips for Cybersecurity Interview Questions
When crafting your cybersecurity interview examples for cybersecurity interview questions, always use the STARR Method:
- Situation: Set technical context
- Task: Explain security responsibility
- Action: Detail technical and strategic actions
- Result: Share measurable security outcomes
- Reflection: Highlight technical lessons and growth
Essential Principles for Cybersecurity Interview Examples:
- Choose examples that demonstrate both technical and business understanding
- Emphasize collaboration with cross-functional teams
- Focus on measurable security improvements and risk reduction
- Show continuous learning and adaptation to evolving threats
- Keep your answers between 2-3 minutes and demonstrate impact
Practice with InterviewBee
Master cybersecurity interview questions with InterviewBee's AI tools designed specifically for security professionals preparing for security analyst interview questions:
- Mock AI Interviewer: Practice realistic cybersecurity scenarios and get feedback on technical answers
- Live AI Assistant: Get real-time support during actual technical interviews
- Performance Analytics: Track improvement across different cybersecurity domains over time
Conclusion
Cybersecurity interview questions are designed to assess both your technical expertise and practical problem-solving abilities. Whether you're facing security analyst interview questions or challenging pentester interview questions, these proven cybersecurity interview examples and STARR framework answers help you confidently demonstrate your security knowledge and incident response capabilities.
Ready to practice? Try InterviewBee's Mock AI Interviewer for personalized coaching that transforms your cybersecurity interview questions preparation into compelling demonstrations of your expertise.


