
Blockchain Developers: 90% Skip This $125K+ Security Skill
- Author: Anindita Ghosh
- Published On: Aug 3, 2025
- Category:Technical
There's nothing worse than watching someone else land the $178K cryptography role because they "communicated better." Here's the reality: 90% of exploited blockchain projects never had security audits, creating massive demand, yet most brilliant security developers stumble through interviews not because they lack skills, but because they can't structure their expertise under pressure.
According to CertiK's latest security report, while the industry lost $2.36 billion across 760 security incidents in 2024, smart contract developers with security audit expertise are commanding salaries from $125K-$250K globally , with cryptography specialists reaching $300K+. This isn't about developers failing audits, it's about the critical shortage of developers who can perform them.
The Question That Separates Web3 Security Experts from Traditional Coders
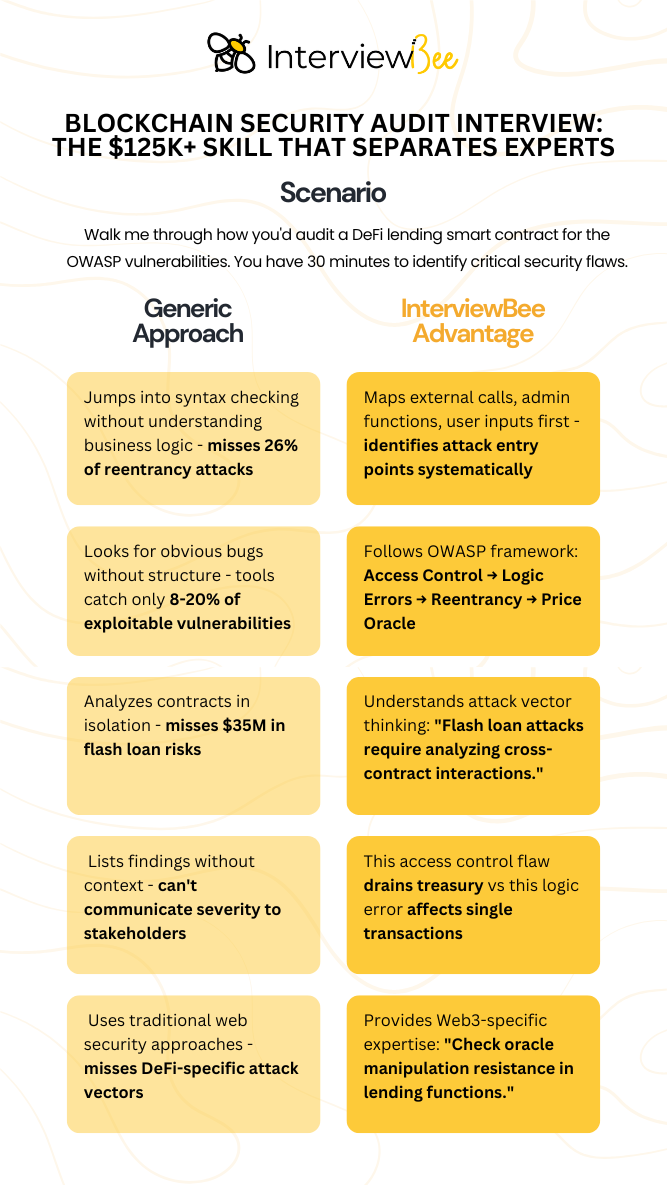
Here's the scenario breaking careers: "Walk me through how you'd audit this DeFi lending smart contract for the OWASP Top 10 vulnerabilities. You have 30 minutes to identify critical security flaws."
This single assessment has become the gateway to Web3 positions at companies like Kraken ($173K-$289K) and Exodus ($150K-$200K). Yet most blockchain developers freeze completely when faced with systematic vulnerability assessment.
Where 90% of Developers Go Wrong
- Code-First, Security-Last: Most developers jump straight into checking syntax without understanding the business logic. They miss that 26% of audited smart contracts still suffer reentrancy attacks because they focus on obvious bugs, not sophisticated attack vectors.
- Missing the OWASP Framework: They fail to systematically check for access control vulnerabilities (which caused $953.2M in losses), price oracle manipulation, or logic errors. Without structured methodology, they miss critical flaws that automated tools can't detect-tools only catch 8-20% of exploitable bugs.
- No Threat Modeling: Developers analyze code in isolation without considering how attackers actually exploit DeFi protocols. They don't understand that flash loan attacks ($35M in losses) require analyzing cross-contract interactions.
The Framework That Lands $125K+ Offers
Successful Web3 security specialists follow the OWASP Smart Contract Top 10 methodology:
- Threat Surface Analysis (5 minutes): List all the outside functions, administration-oriented functions, and inputs. "I'd first identify all entry points where attackers could interact with the contract."
- OWASP Systematic Review (20 minutes): Check each vulnerability category methodically:
- Access Control: Verify role-based permissions and function modifiers
- Logic Errors: Analyze business logic for manipulation possibilities
- Reentrancy: Test all external calls for callback vulnerabilities
- Price Oracle: Evaluate oracle dependencies for manipulation risks
- Risk Assessment (5 minutes): Prioritize findings by potential impact. "This access control flaw could drain the entire treasury, while this logic error only affects individual transactions."
This systematic approach demonstrates the security thinking that distinguishes Web3 specialists from regular blockchain developers.
How InterviewBee Elevates Your Security Assessment
When facing complex Web3 security questions, InterviewBee provides structured audit frameworks in real-time:
- Instant OWASP Structure: The moment you hear "smart contract audit," InterviewBee prompts: "Start with access control analysis, then check for reentrancy patterns, followed by logic error assessment."
- Vulnerability-Specific Guidance: For each OWASP category, it suggests specific checks: "Look for missing onlyOwner modifiers in critical functions" or "Verify CEI pattern in all external calls."
- Web3-Specific Intelligence: InterviewBee understands DeFi nuances, suggesting: "Check for flash loan attack vectors in lending functions" and "Verify oracle price manipulation resistance."
Conclusion
Security assessment skills remain the highest-paid specialty in Web3 development. With an average of 223 applicants per Web3 job, competition is fierce but rewards are substantial for those who master security expertise.
Companies need developers who can prevent the next $2.36 billion in losses, not just write smart contracts. Master the OWASP framework, and you'll join the elite minority commanding premium salaries in cryptography and security roles.
Ready to become a Web3 blockchain developer with security specialization? Try InterviewBee for free and transform vulnerability assessments into career-defining opportunities.


